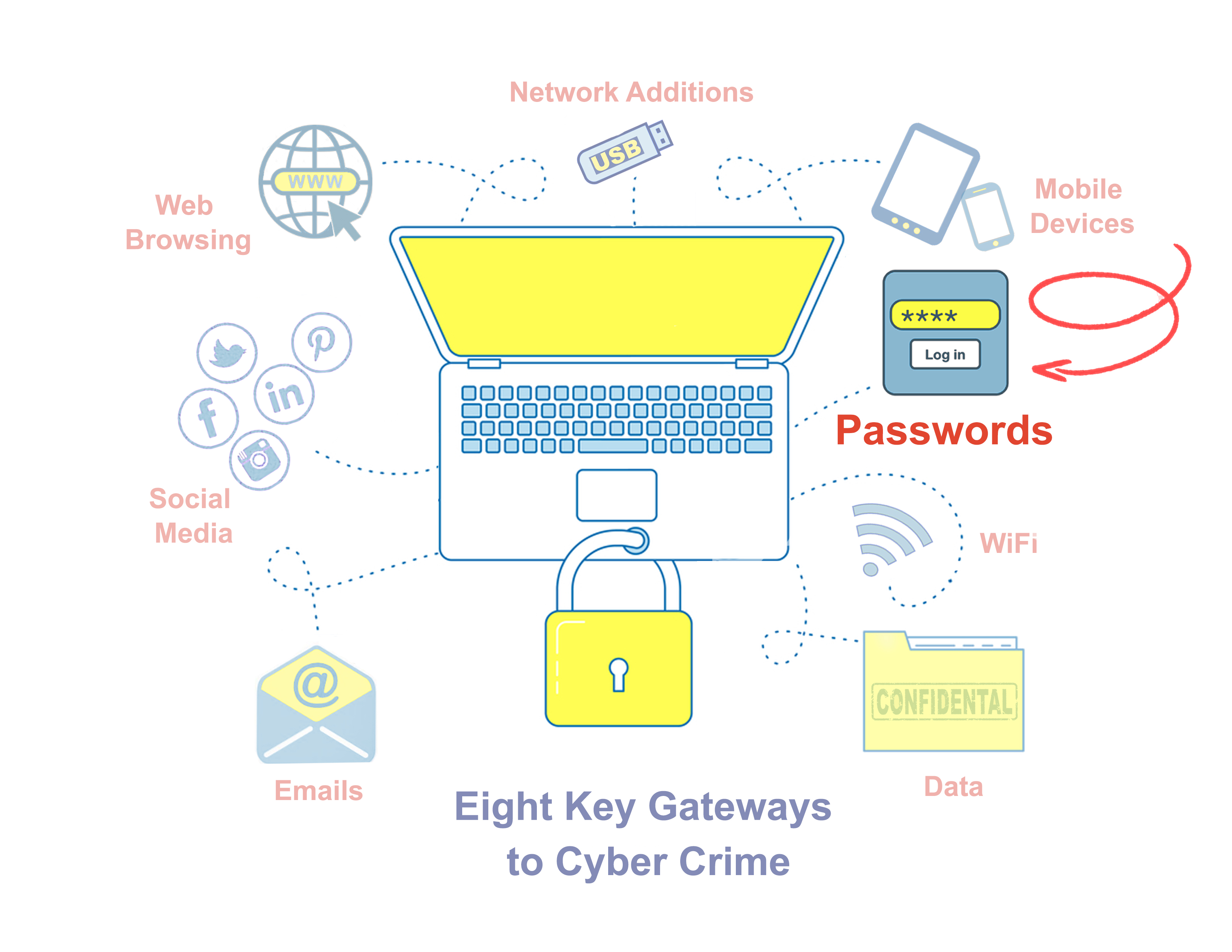
This is the first in a series of articles focusing on practical ways to block key Cyber Crime Gateways.
Do you know how to create an unbreakable password that also meets compliance requirements? Test yourself with these questions then click the Read More for the answers.